What is a RADIUS Server and RADIUS Authentication (Explained)
Cloud technology has been one of the most significant technological phenomena in the past decade. It has revolutionized a wide variety of fields, like software development or artificial intelligence research. It has made communication much faster and enabled other technological breakthroughs like big data. In the current era, hardly any domain has not utilized cloud technology to grow their business. Cloud security is one of the areas that every IT professional should consider, especially when it comes to authentication and user access. One such area that has shown huge growth is Wireless Authentication using RADIUS.
As mighty as cloud technology may seem, it has several working cogs inside it, just like any technology. Robust network computing strategies and technologies are the reason behind the magic of cloud technology. Anyone wanting to understand it better will have to learn the fundamentals of computer networking, like servers and client/server communication protocols. One of the most critical client/server protocols is RADIUS.
This article will take you through what RADIUS server protocol is and why it is implemented. It will explore its background and the advantages it brings. The article will also discuss different steps of how RADIUS works and use cases for implementing the RADIUS protocol.
What is RADIUS Server ?
RADIUS is the Remote Authentication Dial-In User Service protocol. It was developed by the American remote-access networking equipment manufacturer Livingston Enterprises. RADIUS is a centralized server authentication and accounting protocol based on the User Data protocol, which facilitates easy messaging between devices on a network.
The main job of a RADIUS server is to receive client requests and relay configuration information needed by the client to deliver some service to the user. It supports different methods of authenticating a user, such as CHAP, PPP, and UNIX login. The authentication and authorization happen simultaneously, with the RADIUS server sending attribute-value pairs along when it sends an ‘Access-Accept’ response.
The RADIUS server also provides accounting features independently. Data at the start and end of connection sessions can be provided by the RADIUS server, detailing the resources and their amounts used. A shared secret accomplishes the authentication of transactions between the client and the RADIUS server that the network never knows.
Devices supporting the RADIUS protocol can handle issues like server availability, retransmission, and timeouts themselves. Unlike other devices, the transmission protocol doesn’t cover such scenarios for them. Other protocols similar to RADIUS include Lightweight Directory Access Protocol (LDAP) and the MIT-developed Kerberos.
What is RADIUS Authentication
RADIUS Authentication and Authorization Explained

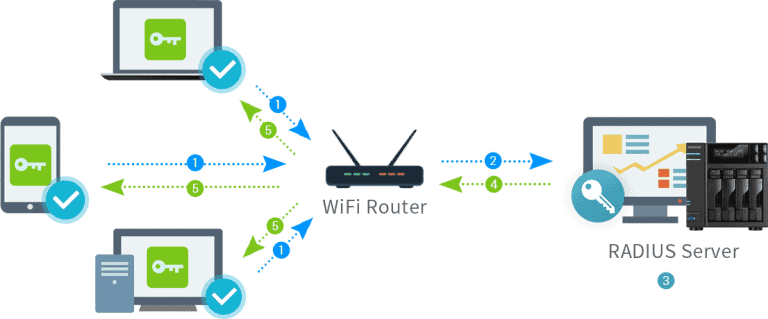
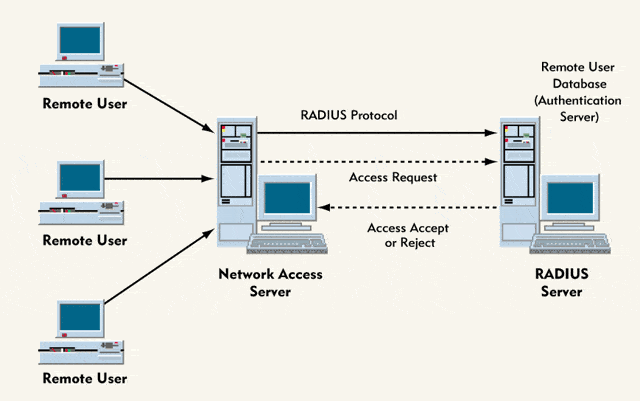
The RADIUS server protocol involves interaction between the server, RADIUS client, and a dial-in user. Without going into too many technicalities, a simplified version of the interaction is as follows:
- The user initiates a direct point-to-point (PPP) authentication to the network access server (NAS). The NAS is actually the RADIUS client, and the PPP authentication doesn’t involve any network in between.
- The RADIUS client prompts the user for username and password.
- The user replies back.
- The RADIUS client sends the username and the encrypted password to the RADIUS server to authenticate the user using different mechanisms. The server goes through a database to locate the username and, if not found, sends an ‘Access-Reject’ message. The rejection can come with a text message explaining the refusal.
- The server replies back with an appropriate ‘Access-Accept’ or ‘Access-Reject’ response after authentication. It can also be sent by a ‘Challenge’ if the Challenge Handshake Authentication Protocol (CHAP) is used.
- The RADIUS client acts on the service parameters and services that come bundled with the ‘Accept’ or ‘Reject’ response.
Want to Deploy a RADIUS Server ?
Try deploying our RADIUS Server solution into Azure, AWS or GCP and test it out for yourself.
RADIUS Accounting
The process for accounting through the RADIUS server begins during the process highlighted above. When the user receives access to the RADIUS server, the NAS sends a RADIUS Accounting-Request packet to the server. It contains the user ID, point of access, unique session identifier, and network address. The point during the session when the accounting initiates is termed an Accounting Start.
Apart from the initiating Accounting-Request packet, it is possible to send another packet midway to receive an interim update. The packet sent during the session updates the session’s status by collecting the session duration and data usage.
Once the session has ended, a final packet, called the Accounting Stop record, is sent and provides overarching information like total data received and transferred, reasons for disconnection (if any), and total session duration. It is followed by an Accounting-Response acknowledgment, leading to all data about the session being stored on the RADIUS server.
How is RADIUS Server Used?
The RADIUS server protocol is commonly used for all sorts of different authentication and authorization purposes related to communication networks. According to the popular RADIUS server freeRADIUS, the protocol handles one-third of the authentications on the Internet. Some of its popular uses are discussed below in brief:
- The RADIUS server can be utilized as a proxy client that connects to and receives data from other RADIUS servers or different authentication server instances. As a proxy, it can redirect or manage traffic meant for a different server and can determine where the request is sent.
- The user passwords sent between the RADIUS client and server are encrypted as per the protocol. The encryption lessens the chances of someone stealing the password over an insecure network. However, the user password is the only encrypted part while all other information exchanged, like username and accounting data, can be potentially stolen.
- The RADIUS server protocol is utilized by cloud platforms as well. For example, Microsoft Azure provides a multi-factor authentication server that can act as a RADIUS server. Another article on our blog shows RADIUS Server Windows setup for wireless authentication using Active Directory.
- The simple nature of the RADIUS server protocol results in clients having lower memory, storage, and CPU requirements than other clients like SQL or OBDC connectors. However, the RADIUS server can support complex conversations and maintain the user state even if the authentication involves multiple rounds of requests.
- The RADIUS server can change the authorization of users whenever needed, also known as ‘asynchronous calling’. The attributes it sends over on acceptances are well-defined and supported by virtually all network devices.
- With the rise in work-from-home due to the recent pandemic, companies globally have started using VPNs to ensure network security. A significant number of enterprises use RADIUS protocol to authenticate user access to their VPNs. However, most guides recommend having additional measures as RADIUS can also fall weak to some vulnerabilities.
Securing a Network with RADIUS Server Security
Cybersecurity has seen a sharp increase in interest from enterprises of all scales globally. After all, data breaches and DDoS attacks have become extremely common. With each passing year, new network security measures and protocols are developed to fight against every kind of vulnerability there is. With network technology getting more robust, it is evident that security measures and challenges will also get more challenging.
In the case of cloud technology, security is a fundamental part. Cloud security is crucial to any kind of cloud strategy, be it multi-cloud or hybrid cloud. While pretty old in age, the RADIUS server security protocol continues to serve the Internet and the cloud. As the Internet gets more secure, we will indeed move on to more robust protocols soon.
Related Posts:
- How to Setup AWS RADIUS Server (NPS) Cloud RADIUS for Wireless Authentication
- How does RADIUS Server Authentication Work? Using NPS Server
- How to Setup RADIUS Server in Azure for Wireless Authentication
- How Does PKI Authentication Work? With Authentication Flow Diagram
- Advantages of RADIUS WiFi Authentication
- What are RADIUS Authentication Methods / Protocols Used

